I believe the Open Container Initiative (OCI) is a step in the right direction, but I still think Docker Inc. needs to nurture and allow the community to innovate….
docker pull myfinger


I believe the Open Container Initiative (OCI) is a step in the right direction, but I still think Docker Inc. needs to nurture and allow the community to innovate….

Background So lately, I have been hearing a lot about containers vs. virtual machines and I wanted to get in on the action. I saw the a recap of Alex Polvi’s session at OpenStack Silicon Valley and I was inspired. I agree with Alex, and for fun, I wanted to state all of his points

Hey all, come join Red Hat and Kismatic at the first community driven, technical event dedicated entirely to Kubernetes.

Red Hat Summit and DevNation are next week.

The Linux Foundation has launched ContainerCon to bring together leading contributors in Linux containers, the Linux kernel, and related projects to forge a path to continued innovation and education.

Red Hat Summit and DevNation are next week.

Background As part of my blog series on Running Docker in Production, I have been writing about Docker security. Coincidentally, the CIS Docker 1.6 Benchmark v1.0.0 was released at the end of May and I thought it would be fun to tackle this new security benchmark. The CIS Docker Benchmark is meant to be a
Continue Reading “Meeting the CIS Docker Benchmark with RHEL7 and RHEL Atomic”
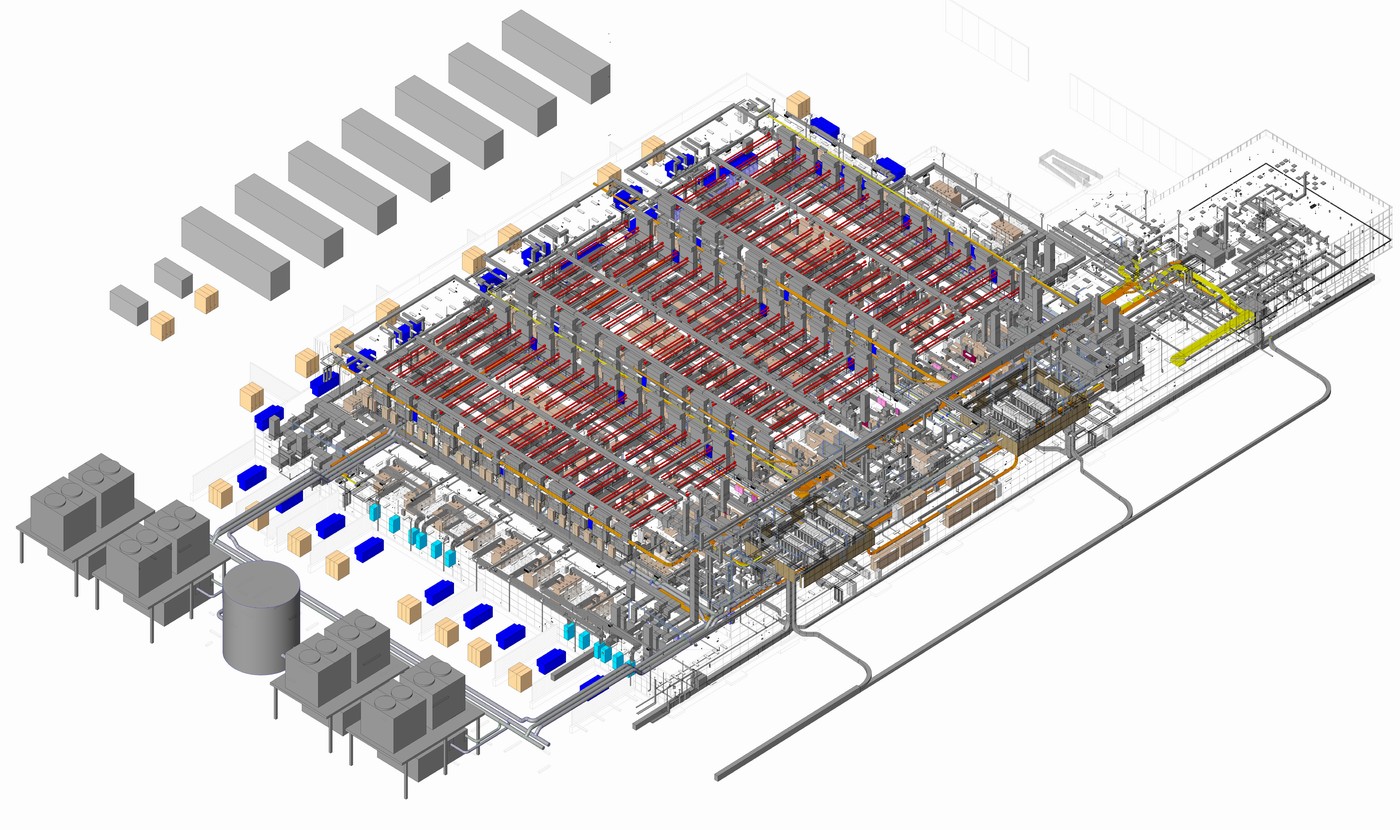
Background This blog series is focused on programmers, systems administrators, and application administrators that want to run Docker in production. The subject matter ranges from workflow and practical guidelines to security and best practices in manageability. A Practical Introduction to Docker Containers A Practical Introduction to the Docker Registry Server Core Builds in the
Background As has been stated before, Docker containers do not contain all of the parts of the operating system necessary to be considered secure. That said, the advantages of using them is so compelling that many companies, large and small, have began to investigate how to run containers in a production environment. I would argue
Continue Reading “Securing Docker Containers with sVirt and Trusted Sources”

This presentation is a 16 slide introduction to what must be thought about when building a production cloud. Proper image management is critical engineering task.