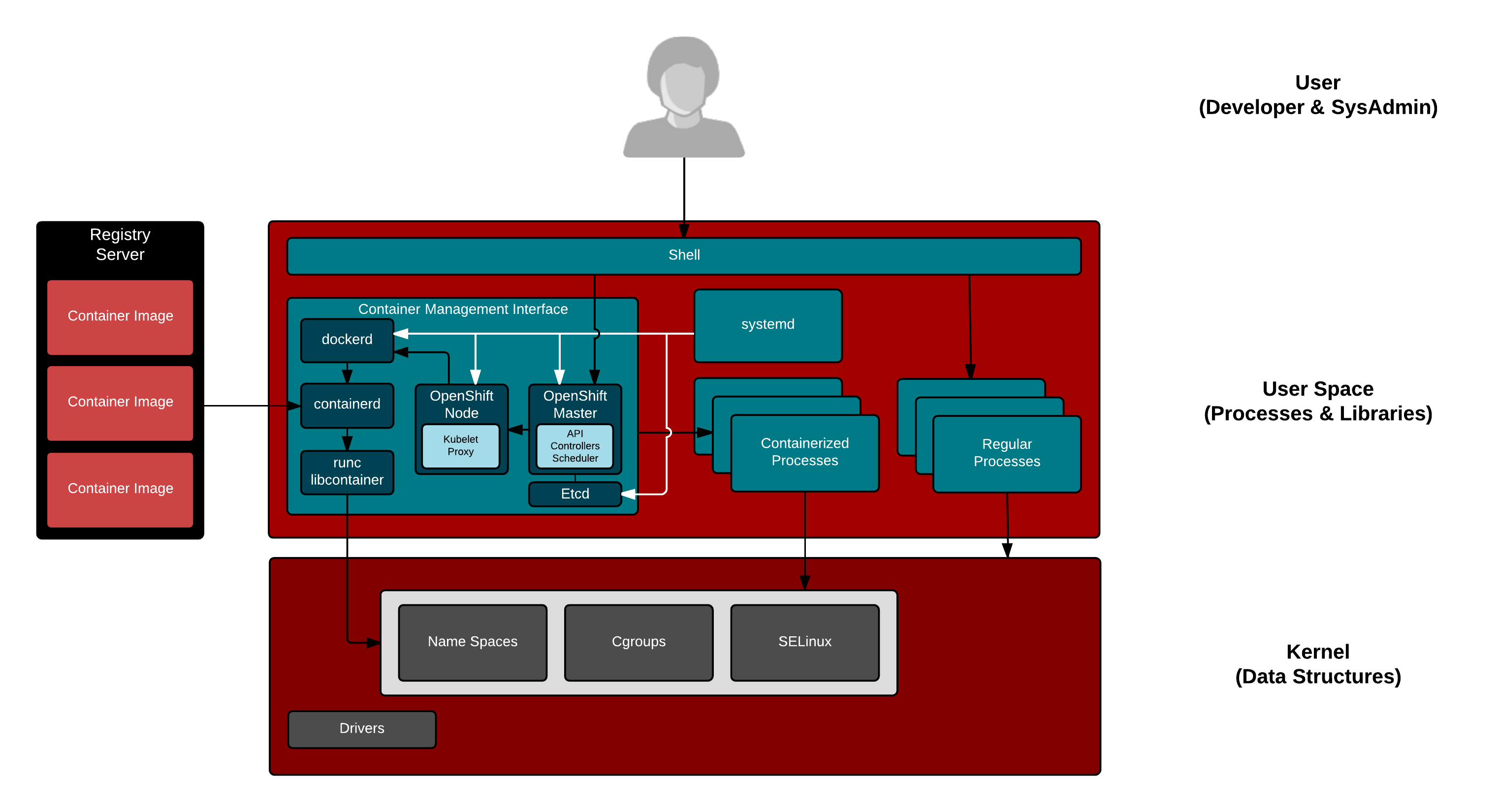
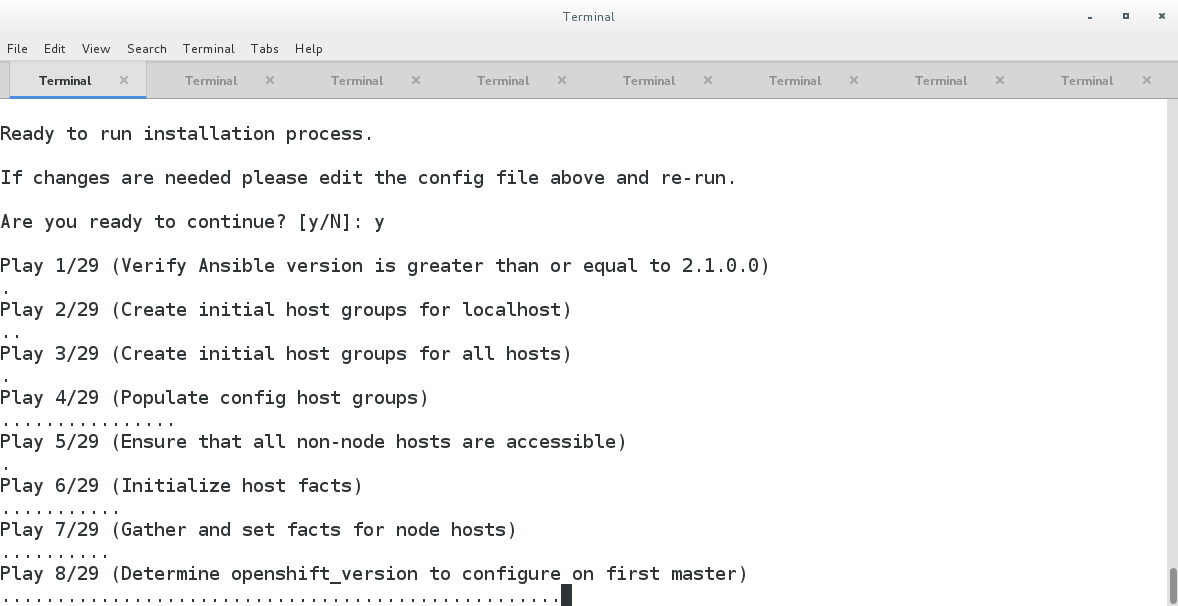
Background Have you ever tried to get runc to work? Did you have that WTF moment where you were like, this is weird, and annoying, and why do I even need to know this? When, I use docker, everything just works. Well, I am here to help. Why might you want to get ninja with
Getting Ninja with Runc